Deploy Applications Using the AWS EKS EC2 ASG CTO.ai Workflow via CDK
Scroll DownThe AWS Cloud Development Kit (AWS CDK) is an open-source software development framework for defining cloud infrastructure in code and provisioning it through AWS CloudFormation. The CDK allows developers to model and provision AWS resources using familiar programming languages such as TypeScript, JavaScript, Python, Java, and C#.
Using AWS CDK, you can create reusable, shareable components called "constructs" that can represent a single resource or a group of resources that work together. These constructs can be combined to define complex cloud infrastructure in a modular, scalable way.
The CDK has a few key components: Constructs: These are the basic building blocks of AWS CDK apps.
- A construct represents an AWS resource or a group of resources working together.
- Stack: A stack is a deployment unit in AWS CDK that contains a set of resources defined within the scope of the stack. It maps to an AWS CloudFormation stack, which manages the lifecycle of the resources.
- App: An app is a top-level container for one or more stacks in the AWS CDK. It is responsible for synthesizing the AWS CloudFormation templates and deploying the stacks.
With the AWS EKS EC2 CDK workflow, you can deploy and create reusable components in your infrastructure. This promotes a standardized way of building your existing and new cloud infrastructure and reduces the need to rewrite code for similar tasks. The CTO.ai AWS EKS EC2 workflow seamlessly integrates with other AWS services. This makes it easy to build end-to-end CI/CD pipelines and automate deployment processes.
In this tutorial, you’ll learn how to configure and deploy resources with the EKS EC2 Workflow.
Prerequisites
- Access to CTO.ai Account and CTO.ai CLI installed on your local machine
- Docker installed on your local machine
- Access to AWS Account and AWS CLI installed on your machine
Setup AWS Access Keys and GitHub Secrets
In this tutorial, you’ll be creating the AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY secret keys from your IAM console in the AWS dashboard and attaching your AWS_ACCOUNT_NUMBER to the CTO.ai secrets vault. Also, generate your GitHub token from Github by going to Settings → Developer settings → Personal access tokens → Generate new token on your Github profile.
- Next, add all secret keys to your CTO.ai account secret dashboard.
Configure the Ops.yml file
The AWS EKS EC2 ASG workflow is open-source on GitHub, and you can install it by cloning the repository.
git clone https://github.com/workflows-sh/aws-eks-ec2-asg-cdk.git
Cd aws-eks-ec2-asg-cdkTo build and set up the EC2 EKS ASg infrastructure, you’ll have to configure the ops.yml file with the appropriate commands to set up, deploy and destroy your infrastructure. In the ops.yml configuration below, you can see the YAML configuration file defining a set of commands. Each command has a name, description, a script to run, a description, and environment variables. The environment variables are divided into static, secrets, and configs.
version: "1"
commands:
- name: setup-aws-eks-ec2-asg-cdk:0.1.2
run: ./node_modules/.bin/ts-node /ops/src/setup.ts
description: "setup an environment"
env:
static:
- STACK_TYPE=aws-eks-ec2-asg-cdk
- AWS_REGION=us-west-1
secrets:
- AWS_ACCESS_KEY_ID
- AWS_SECRET_ACCESS_KEY
- AWS_ACCOUNT_NUMBER
configs:
- DEV_AWS_EKS_EC2_ASG_CDK_STATE
- STG_AWS_EKS_EC2_ASG_CDK_STATE
- PRD_AWS_EKS_EC2_ASG_CDK_STATE
- name: deploy-aws-eks-ec2-asg-cdk:0.1.1
run: ./node_modules/.bin/ts-node /ops/src/deploy.ts
description: "deploy to an environment"
env:
static:
- STACK_TYPE=aws-eks-ec2-asg-cdk
- AWS_REGION=us-west-1
secrets:
- AWS_ACCESS_KEY_ID
- AWS_SECRET_ACCESS_KEY
- AWS_ACCOUNT_NUMBER
configs:
- DEV_AWS_EKS_EC2_ASG_CDK_STATE
- STG_AWS_EKS_EC2_ASG_CDK_STATE
- PRD_AWS_EKS_EC2_ASG_CDK_STATE
- name: destroy-aws-eks-ec2-asg-cdk:0.1.1
run: ./node_modules/.bin/ts-node /ops/src/destroy.ts
description: "destroy an environment"
env:
static:
- STACK_TYPE=aws-eks-ec2-asg-cdk
- AWS_REGION=us-west-1
secrets:
- AWS_ACCESS_KEY_ID
- AWS_SECRET_ACCESS_KEY
- AWS_ACCOUNT_NUMBER
- name: ssh-aws-eks-ec2-asg-cdk:0.1.0
run: ./node_modules/.bin/ts-node /ops/src/ssh.ts
description: "connect to bastion with ssh"
env:
static:
- STACK_TYPE=aws-eks-ec2-asg-cdk
- AWS_REGION=us-west-1
secrets:
- AWS_ACCESS_KEY_ID
- AWS_SECRET_ACCESS_KEY
- AWS_ACCOUNT_NUMBER
- name: tunnel-aws-eks-ec2-asg-cdk:0.1.0
run: ./node_modules/.bin/ts-node /ops/src/tunnel.ts
description: "connect to bastion with ssh"
env:
static:
- STACK_TYPE=aws-eks-ec2-asg-cdk
- AWS_REGION=us-west-1
secrets:
- AWS_ACCESS_KEY_ID
- AWS_SECRET_ACCESS_KEY
- AWS_ACCOUNT_NUMBER
- name: vault-aws-eks-ec2-asg-cdk:0.1.0
run: ./node_modules/.bin/ts-node /ops/src/vault.ts
description: "manage secrets vault"
env:
static:
- STACK_TYPE=aws-eks-ec2-asg-cdk
- AWS_REGION=us-west-1
secrets:
- AWS_ACCESS_KEY_ID
- AWS_SECRET_ACCESS_KEY
- AWS_ACCOUNT_NUMBER
configs:
- DEV_AWS_EKS_EC2_ASG_CDK_STATE
- STG_AWS_EKS_EC2_ASG_CDK_STATE
- PRD_AWS_EKS_EC2_ASG_CDK_STATE
help:
usage: ops run vault <sub-cmd> <--key> <--value>
arguments:
init: 'init the environments vault'
set: 'set a key in the enviroment vault'
ls: 'list keys in the environment vault'
rm: ' remove a specific key in the environment vault'
destroy: 'destroy the environment vault'There are six commands defined in this configuration file:
- setup-aws-eks-ec2-asg-cdk:0.1.2: This command sets up an environment for the AWS EKS cluster with EC2 instances in an ASG using CDK.
- deploy-aws-eks-ec2-asg-cdk:0.1.1: This command deploys the configured environment to the AWS EKS cluster with EC2 instances in an ASG using CDK.
- destroy-aws-eks-ec2-asg-cdk:0.1.1: This command destroys the environment created in the AWS EKS cluster with EC2 instances in an ASG using CDK.
- ssh-aws-eks-ec2-asg-cdk:0.1.0: This command connects to a bastion host using SSH.
- tunnel-aws-eks-ec2-asg-cdk:0.1.0: This command establishes a tunnel to a bastion host using SSH.
- vault-aws-eks-ec2-asg-cdk:0.1.0: This command manages a secrets vault for the environments.
Setup and Build Environment
Next, set up the environment on your CLI by running the ops run -b . command and selecting setup - setup an environment. This will provision the AWS EKS EC2 stack using Cloud Formation.
- Enter the name of your environment, application repo name, and branch name.
- The workflow will start deploying and creating your resources on AWS using CloudFormation.
View Resources in CloudFormation
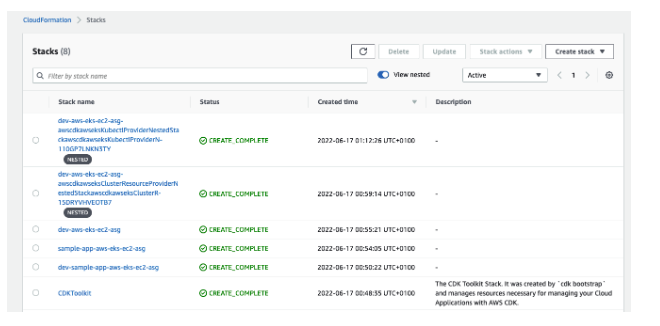
After deploying your AWS EC2 EKS and ASG workflow, you can see your stack directly on AWS CloudFormation. In your CloudFormation Stack, you can see your AWS resources created:
- Dev-AWS-EKS-ASG-Provider
- AWS-EKS-EC2-ASG Resource
- Dev-AWS-EKS-EC2-ASG
- Sample-App-AWS-EKS
- CDKToolkit
- Dev-Sample-App-AWS-EKS-EC2-ASG
View EC2 instances on AWS
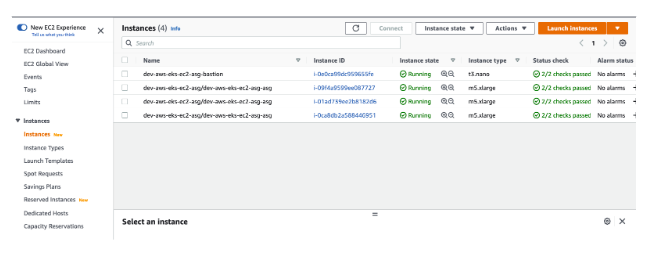
Back in your AWS console, you can see your EC2 instances running. The AWS EC2 Workflow creates four instances for you:
- dev-aws-eks-ec2-asg-bastion
- dev-aws-eks-ec2-asg/dev-aws-eks-ec2-asg-asg
- dev-aws-eks-ec2-asg/dev-aws-eks-ec2-asg-asg
- dev-aws-eks-ec2-asg/dev-aws-eks-ec2-asg-asg
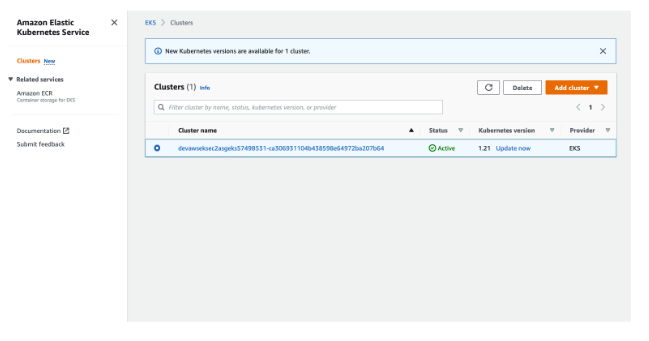
View EKS Cluster in AWS Console
Next, in your EKS console, you’ll see your EKS cluster created. With the EKS cluster, you can run Kubernetes without installing, managing, or maintaining your own Kubernetes control plane.
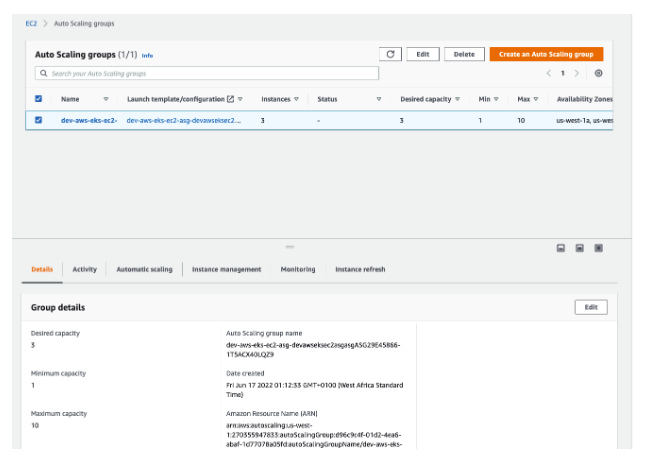
View Auto Scaling Groups
In your EC2 dashboard, you can see your auto-scaling groups instances and status.
AWS Auto Scaling schedules the scaling actions that proactively increase and decreases the capacity to match the load forecast. At the scheduled time, AWS Auto Scaling updates the minimum capacity with the value specified by the scheduled scaling action.
Master Application Deployment with our AWS EC2 EKS CDK Workflow
Don't miss out on the benefits of seamlessly deploying your applications using the AWS EC2, EKS, and ASG workflow with CDK! Take the leap now and revolutionize your deployment process, saving time and resources. Empower your team with the cutting-edge AWS EC2 EKS ASG workflow. Sign up now and stay ahead of the curve!

Comments